Introduction#
In today's wave of digitalization, the strategic importance of Application Programming Interfaces (APIs) is increasingly prominent. APIs are not just bridges for communication between modern software and internet services; they are also at the core of value creation for enterprises. With the rapid development and widespread application of APIs, security issues have emerged, particularly API abuse, which has become a critical challenge that needs to be addressed in the field of digital security.
Traditional cybersecurity models are based on defined security boundaries, but in the context of hybrid clouds and mobile work, this concept is being redefined. More and more organizations are beginning to adopt the principles of Zero Trust Architecture (ZTA), which centers on not defaulting to trust any user or device but instead requires evaluation for every access to sensitive resources and continuously monitors their trustworthiness. However, in many implementations of ZTA, the sensitive application functions and data access methods based on APIs are often overlooked, which is particularly evident when designing continuous trust assessment mechanisms. To fill this gap, we need to place a high emphasis on API security and ensure that they are adequately considered and protected under the Zero Trust Architecture.
In this article, we will explore why API abuse constitutes a unique problem, how it affects the business logic and data security of enterprises, and discuss how to incorporate API security into the Zero Trust Architecture to build a more robust and flexible security strategy. By analyzing the intersection of these two areas in detail, we can not only better understand the security threats posed by APIs but also provide enterprises with a series of practical protective measures to help them remain invulnerable in this ever-changing digital world.
New Challenges of API Abuse#
In the process of building a Zero Trust Architecture, APIs, as an indispensable component of information systems, are particularly critical for security. However, with the evolution of technology, API abuse has become a new type of challenge in the security field. This abuse is not a traditional security vulnerability attack but rather a malicious entity exploiting APIs to perform unintended operations, which is particularly difficult to defend against under the Zero Trust philosophy.
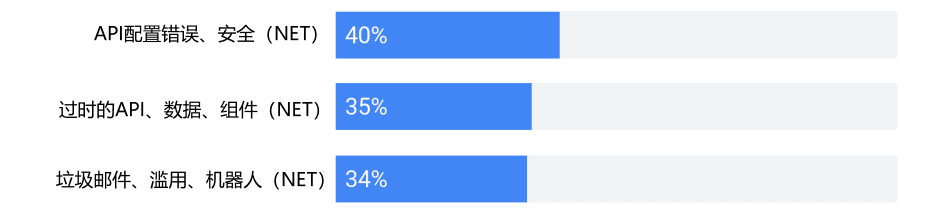
Figure: Sources of API Security Threats - Google Cloud's API Security Report
According to OWASP's Top Ten API Security Risks of 2023 report, the risks posed by API abuse can be as severe as traditional security threats. Abusers leverage legitimate access rights to operate as legitimate users, making it difficult to distinguish this behavior from normal activities in system logs, presenting a significant challenge to traditional intrusion detection systems. Under the Zero Trust Architecture, every access attempt must undergo strict trust evaluation, which essentially requires us to adopt more proactive and comprehensive protective measures for API security. In addition to continuous monitoring and evaluation, organizations need to employ more advanced data analysis methods, such as behavioral analysis and machine learning techniques, to identify and prevent API abuse. For example, Akamai suggests that through powerful computing capabilities, the SaaS model can analyze large-scale datasets to effectively identify anomalous behaviors in API usage, which is a key aspect of achieving continuous verification principles in Zero Trust.

Currently, defending against API abuse requires not only technological innovation but also thoughtful planning at the policy and strategic levels. In this ever-changing security environment, we must reassess our API security strategies to ensure they can integrate with the core principles of Zero Trust Architecture to address increasingly complex threats. Within the Zero Trust framework, no device or user is considered trusted by default, which necessitates a complete redesign of our API management strategies. From API discovery, authentication, and authorization to behavior monitoring and anomaly detection, every aspect must strictly adhere to Zero Trust principles. Through this comprehensive strategy, we can better prevent API abuse and protect the critical business processes of enterprises from threats.
In the future, as the Zero Trust concept deepens and technology continues to evolve, API security strategies will become more intelligent and automated. However, today, we must take practical steps to prepare for these challenges.
Basic Principles of Zero Trust Architecture#
In a Zero Trust Architecture, the principle of "never trust, always verify" establishes a new foundation for enterprise security. This architecture does not rely on traditional perimeter defenses but implements strict identity verification and access control for every resource access. This shift is particularly crucial for API security, as APIs are key channels for data and service interaction in modern enterprise IT architectures. The core of Zero Trust Architecture lies in eliminating the trust distinction between internal and external networks, requiring strict security checks for all access behaviors within the network, regardless of whether the access request originates internally or externally. This model assumes that security threats can come from anywhere, thus necessitating continuous security verification for every access request. For enterprises, this means implementing security controls at every network node, every data flow, and every API call to ensure the safety of data and resources.

Under the Zero Trust framework, API security becomes a critical support for achieving security goals. Each API is a potential access point that needs to be strictly controlled and monitored. The following are key points at the intersection of Zero Trust principles and API strategies:
- Authentication: In a Zero Trust Architecture, all API calls require strong verification to ensure that only authenticated and authorized users and systems can access the API.
- Least Privilege: Access permissions for each API should be limited to the absolute minimum necessary to reduce security risks associated with excessive permissions.
- Dynamic Policies: API access policies should be dynamically adjusted based on the access context, reflecting the risk level of the access request and the trustworthiness of the user and system in real-time.
- Continuous Monitoring: Real-time monitoring of API usage and analysis of access patterns to quickly identify and respond to anomalous behaviors and potential security threats.
By implementing these strategies, APIs not only serve as bridges for service and data interaction but also become key components in the implementation of Zero Trust Architecture. This ensures that enterprises can maintain robust security defenses in an open and flexible IT environment, providing a solid security foundation for their digital transformation.
Seven Fundamental Principles of Zero Trust and API Security#
The following table includes the seven fundamental principles of ZTA defined in NIST SP 200-807, along with recommendations for aligning an organization's API security practices with these principles.
| Seven Fundamental Principles of Zero Trust Architecture | API Security Vulnerabilities |
|---|---|
| 1. "All data sources and computing services are treated as resources." | Many applications and data sources within the scope of ZTA can be accessed via APIs in addition to direct user interfaces. Therefore, your ZTA assessment and policy execution model should include API interfaces. |
| 2. "All communications are secure, regardless of network location." | Even if APIs are only used internally within private data centers or cloud environments, you should implement encryption, authentication, and authorization as if they were external to ensure the confidentiality and integrity of data. |
| 3. "Access to individual enterprise resources is granted by session." | You should assess trust before granting access to API resources. Access should be granted with the least privilege necessary. Use behavioral analysis to monitor API usage and continuously assess trust. |
| 4. "Access to resources is determined by dynamic policies—including client identity, application/service, and observable state of request assets—and may include other behavioral and environmental attributes." | To apply ZTA to APIs, you must be able to identify the entities involved, infer business context, and use behavioral analysis to identify deviations from normal usage patterns. One notable behavioral attribute is denial of service through rapid API calls. This is why the lack of API rate limiting is classified as unrestricted access to sensitive business flows in the (OWASP) API Security Top 10. As NIST points out, "These rules and attributes are based on the needs of business processes and acceptable risk levels." |
| 5. "Enterprises monitor and measure the integrity and security status of all owned and related assets." | This requirement is based on the Continuous Diagnostics and Mitigation (CDM) concept defined by the U.S. Cybersecurity and Infrastructure Security Agency (CISA). CDM includes elements such as asset management, vulnerability management, and configuration/settings management. Just like physical assets, APIs must be continuously discovered, classified, and tracked. Similarly, continuous vulnerability assessments should go beyond traditional network and application security vulnerabilities to include potential API-based vulnerabilities. |
| 6. "All resource authentication and authorization are dynamic and strictly enforced before access is allowed." | This concept can and should be extended to APIs. Organizations adopting ZTA should continuously monitor API usage and respond to detected anomalies or abuse behaviors in authenticated and authorized API traffic using automated technologies (e.g., blocking, throttling, revoking credentials). |
| 7. "Enterprises collect as much information as possible about the current state of assets, network infrastructure, and communications, and use this information to improve their security posture." | To be an effective component of ZTA, your API security measures must be capable of capturing data over extended periods—ideally, enough time to detect subtle API abuse. This level of detail is necessary for performing behavioral analysis for real-time risk assessment and continuous improvement of ZTA design. This includes providing threat hunters with on-demand access to API and threat data for identifying potential policy improvements. Similar integration points should also be created using the development and operational tools and workflows your team uses. |
Under the Zero Trust Architecture, APIs are not just pipelines for data exchange; they are key resources for maintaining enterprise security. Implementing the fundamental principles of Zero Trust requires us to view API security strategies from a new perspective, ensuring that each principle is reflected in API management.
First, treating all data resources and computing services as resources means that APIs in ZTA should also be included, and each API should undergo the same level of security assessment and policy execution as direct user interfaces. This requires enterprises to conduct comprehensive discovery and classification of APIs, ensuring that every access to API interfaces undergoes strict security review. Second, all communications must be secure, regardless of network location. For APIs, this means that both internal and external APIs should implement encryption, authentication, and authorization to ensure the confidentiality and integrity of transmitted data. Guided by dynamic policies, API access controls should be dynamically adjusted based on the context of the request, including user identity, application status, and other possible behavioral and environmental attributes. This approach helps identify and prevent anomalous behaviors such as denial of service caused by rapid API calls. Monitoring and measuring the integrity and security status of all owned and related assets is particularly important for APIs. This includes real-time tracking of API health and security configurations, as well as continuous vulnerability assessments and mitigations for APIs. All resource authentication and authorization must be dynamically executed and strictly controlled. For APIs, this means that authentication and authorization mechanisms need to adapt to the ever-changing security environment and respond promptly when anomalies or abuse behaviors are detected. Finally, collecting as much information as possible about the state of assets and network infrastructure is crucial for API security. This information helps organizations identify potential abuse behaviors through behavioral analysis and provides data support for continuous improvement of ZTA design.
By applying the above principles, the Zero Trust security model strengthens the security protection of APIs, ensuring the safety of enterprise assets while laying the groundwork for future potential security policy improvements. Under the Zero Trust Architecture, API security is no longer an additional task but a core component of building a robust security system.
Strategies for Defending Against API Abuse#
Under the Zero Trust Architecture, strategies for defending against API abuse are a key part of building a robust security defense. The formulation of these strategies should be based on a deep understanding of API attacks and the analysis and utilization of a large amount of API-related data, which are essential for identifying and preventing API abuse.
Expanding Understanding of API Attacks#
API security should not only focus on preventing unauthorized access or data breaches but also understand other abusive behaviors that attackers may exploit through APIs. Attackers may not directly attack the API itself but may misuse the legitimate functions of the API for malicious purposes, such as causing service disruptions through high-frequency calls or conducting data mining through functional logic abuse. Therefore, security teams must update their understanding of API attacks, considering that these attacks may span multiple systems and services and involve complex business logic.
Analyzing More Data About APIs#
Effective API abuse defense strategies rely on analyzing a large amount of API usage data. This includes, but is not limited to, API call frequency, call times, access sources, and access behavior patterns. By collecting and analyzing this data, security teams can establish baseline behavior models for normal API usage and use deviations from these baselines to identify potential abuse situations. For example, a sudden increase in API traffic may indicate an automated attack or potential data leakage.
Utilizing APIs to Detect Abuse Behavior#
APIs themselves can become tools for detecting API abuse behavior. By implementing advanced monitoring and analysis techniques, such as anomaly detection systems and artificial intelligence algorithms, abuse events can be identified and responded to in real-time. Automated tools and machine learning models can help identify subtle differences between normal API usage patterns and potential abuse, thus preventing abuse without impacting user experience.
By integrating these strategies, security teams can build a comprehensive API abuse defense system. This system requires not only precision and advancement at the technical level but also a close alignment of security strategies with the business processes and API usage patterns of the enterprise to minimize the risk of API abuse without affecting business continuity.
The Role of Technology in Detecting API Abuse#
In a Zero Trust Architecture, the application of technology in detecting API abuse is an important component of safeguarding enterprise security. The following details the limitations of manual monitoring and the key role of AI and machine learning technologies in detecting API abuse.
Manual monitoring of API activity often has limitations, especially when dealing with large-scale data and identifying complex attack patterns. Manual analysis is prone to resource constraints and is difficult to respond to in real-time. Due to the frequent and complex interactions of APIs, it is challenging for manual monitoring to detect abuse behaviors instantaneously, especially when such behaviors occur amidst a large volume of normal traffic. Furthermore, manual monitoring cannot be sustained 24/7 and is susceptible to human fatigue, which may lead to overlooking or misinterpreting key anomalous indicators in the data. As the number of APIs increases and their usage grows, relying on manual monitoring becomes impractical.
AI and machine learning technologies offer a more efficient and precise approach to detecting API abuse. AI algorithms can process and analyze large amounts of data, identifying patterns that may indicate abuse, such as unusual access frequencies or abnormal access patterns. By continuously learning normal API access behaviors, machine learning models can recognize anomalous behaviors, even if these behaviors superficially resemble legitimate usage. To effectively leverage AI and machine learning for abuse detection, establishing a baseline of normal API usage behavior is crucial. These baselines are formed through long-term monitoring of normal usage patterns of APIs, helping to distinguish normal activities from potential abuse activities. Once activities that significantly deviate from baseline behaviors are detected, security systems can immediately trigger alerts and take appropriate preventive measures.
By utilizing these advanced technologies, enterprises can enhance their ability to detect API abuse, reduce reliance on manual monitoring, and improve the speed and accuracy of security teams' responses to potential threats. As AI technology continues to advance, these tools will become smarter, enabling more accurate identification and prevention of API abuse, providing solid technical support for enterprises' API security strategies.
Integrating API Security into Zero Trust Architecture#
The main idea of Zero Trust is to transform central execution points into multiple micro-checkpoints along every path of applications & APIs. Whether it is internal access or external requests, mobile or PC, API calls or HTTP requests, ordinary employees or CEOs, none are to be trusted.
Integrating API security into the Zero Trust Architecture requires ensuring that the core principles of Zero Trust are fully implemented at the API level and reinforced through continuous monitoring and analysis to enhance the security posture. The seven principles of the Zero Trust security model provide a solid framework for API security. These principles guide enterprises on how to handle APIs and their security, ensuring that every security aspect from authentication to authorization, from encryption to monitoring, is not overlooked. Within this framework, each API endpoint is treated as a separate resource, with strict security checks performed for each access to ensure data security and service reliability.
The API data security control based on Zero Trust adopts a traffic proxy gateway model, using a full traffic proxy gateway as a unified entry point, with application proxy modules controlling specific applications and handling various C/S and B/S applications.
To effectively implement Zero Trust principles, enterprises need to carry out continuous API discovery efforts, maintaining an accurate API inventory. This means not only identifying and managing formal APIs but also discovering and controlling unauthorized or "shadow" APIs to eliminate potential security risks that may be overlooked. In addition to API discovery and management, there is a need to develop the capability to analyze large datasets of API traffic. Through this analysis, enterprises can understand normal usage patterns of APIs, thereby identifying anomalous behaviors that may signal security threats, such as abuse or attacks. Finally, integrating threat and trust insights into the strategy engine of the Zero Trust Architecture (ZTA) allows security policies to dynamically adapt to new intelligence and insights. This integration makes security responses more flexible and timely, enabling adjustments to security policies based on real-time data to address the evolving threat landscape.
Through these measures, API security becomes an organic part of the Zero Trust Architecture, not only strengthening security protection at the API level but also providing more comprehensive protection for the digital assets and services of the entire enterprise. As security strategies and technologies continue to advance, enterprises can maintain resilience and competitiveness in this ever-changing digital age.
Conclusion#
In the face of the ongoing evolution of API security challenges, enterprises need to continuously update and strengthen their security measures. This includes not only technological upgrades but also the security team's awareness of the latest threats, adjustments to strategies, and optimization of security tools. As APIs become more prevalent and important, the protection of APIs must keep pace with their development. The importance of integrating abuse prevention measures cannot be overstated. Enterprises need to defend against external attacks while also implementing internal security measures to prevent API abuse. This includes ensuring appropriate access controls, monitoring, and response mechanisms to promptly detect and address any abnormal API usage patterns.
In a Zero Trust world, the direction of API security will trend towards greater intelligence and automation. By leveraging advanced technologies such as artificial intelligence and machine learning, enterprises will be able to more accurately predict and identify security threats, while automated tools will enhance the speed and efficiency of responses to abuse events. Such developments not only improve security levels but also enhance the adaptability and resilience of enterprises, enabling them to maintain a competitive edge in an ever-changing security environment.
In summary, enterprises must adopt comprehensive API security measures under the Zero Trust Architecture to ensure safe and stable development during their digital transformation process. With advancements in security technology and an increased understanding of the value of security, we have reason to believe that future API security management will become more mature and efficient.